Top 5 Network Security Threats Detected via PCAP Analysis
Network security is crucial for safeguarding sensitive data, preventing unauthorized access, and maintaining operational continuity. Through PCAP (Packet Capture) analysis, network professionals can detect and diagnose a wide array of network threats by examining data packets traveling across the network. Tools like A-Packets streamline this process, offering powerful insights into various network protocols and identifying vulnerabilities.
This article explores the top five network security threats that can be detected and mitigated using PCAP analysis. Supported by visual examples and practical applications, we'll delve into common cyber threats and how packet capture tools can protect networks.
DNS Spoofing and Poisoning Attacks
DNS spoofing, also known as DNS cache poisoning, is a type of cyberattack where false DNS records are inserted into the DNS resolver cache, leading users to malicious sites. This attack is often used to intercept sensitive information such as login credentials.
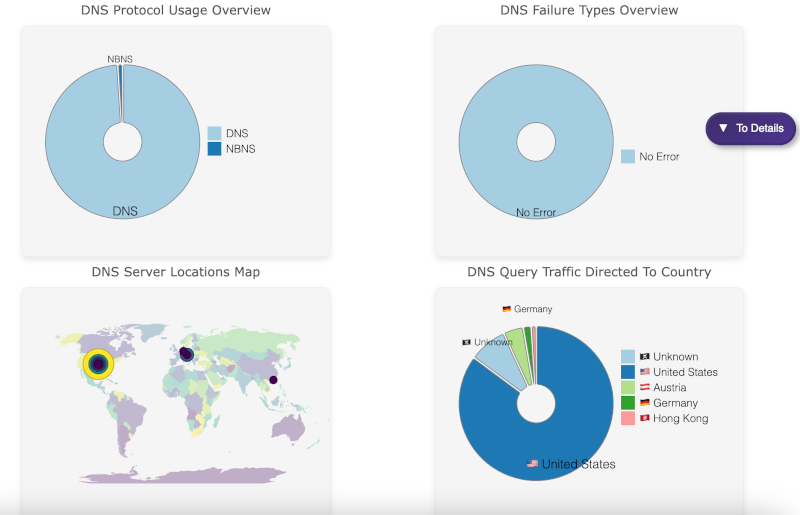
DNS Protocol Usage Overview
The DNS Protocol Usage Overview screen provides an example of how network traffic is classified into DNS, mDNS, and NBNS, enabling network administrators to monitor DNS traffic more closely. By examining DNS queries and responses, PCAP tools can detect irregularities such as unsolicited DNS responses or mismatched IP addresses—common signs of DNS spoofing.
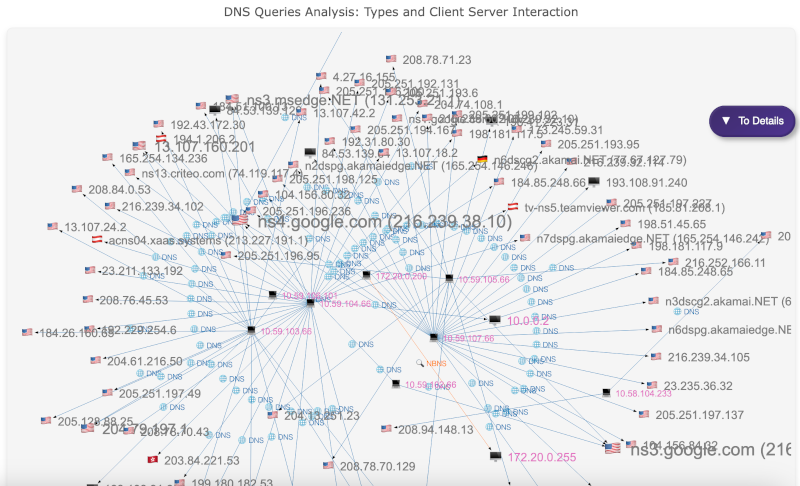
DNS Protocols Net
As shown in the DNS Failure Types Overview, PCAP analysis can identify DNS traffic anomalies and potential poisoning attempts, giving administrators a chance to block malicious DNS servers and reroute legitimate traffic. Early detection of DNS spoofing can prevent users from unknowingly navigating to malicious sites, keeping sensitive data secure.
ARP Spoofing (Man-in-the-Middle Attacks)
ARP spoofing is a man-in-the-middle attack where an attacker associates their MAC address with the IP address of a legitimate device, enabling them to intercept, modify, or block data between devices.
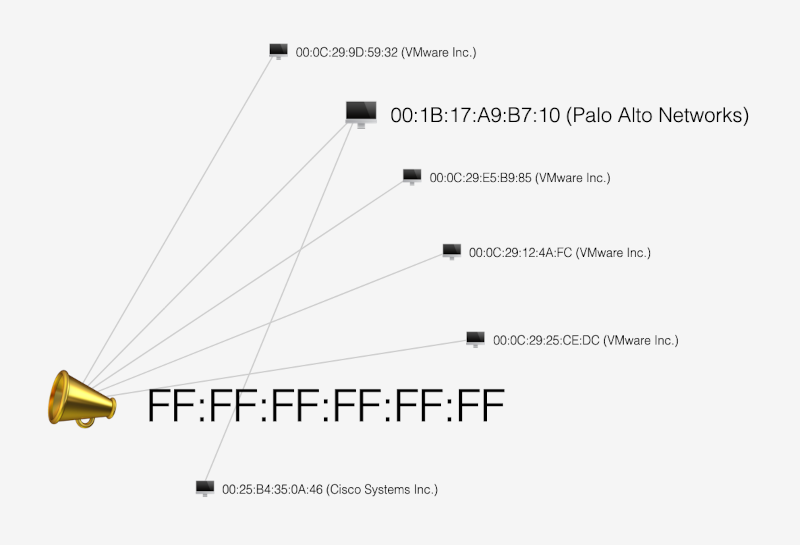
ARP Traffic Visualization
The ARP Traffic Visualization screen offers insight into how communication between devices is depicted, with ARP requests and responses mapped. Gratuitous ARP messages, a red flag for ARP spoofing, can be detected and investigated. Attackers often inject these messages to falsify device identities.
Through PCAP analysis, network administrators can visualize device topology and quickly identify anomalies in the ARP communications, such as unexpected replies or gratuitous ARP messages. Detecting and isolating spoofing devices prevents attackers from monitoring or altering network traffic, thus maintaining the integrity of sensitive communications.
SSL/TLS Attacks and Expired Certificates
SSL/TLS encryption is foundational for securing network traffic, especially for web applications and secure communications. However, vulnerabilities can arise from improperly configured SSL/TLS sessions, weak cipher suites, or expired certificates.
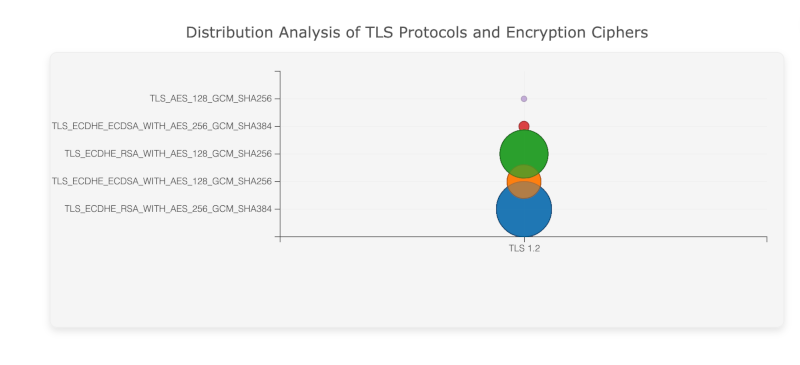
TLS Version and Cipher Suite Distribution
In the Distribution Analysis of TLS Protocols and Encryption Ciphers, we observe which versions of TLS are being used and the corresponding encryption protocols. PCAP analysis helps network administrators detect outdated TLS versions like TLS 1.0, which are more susceptible to attacks such as SSL stripping or cipher downgrade attacks.
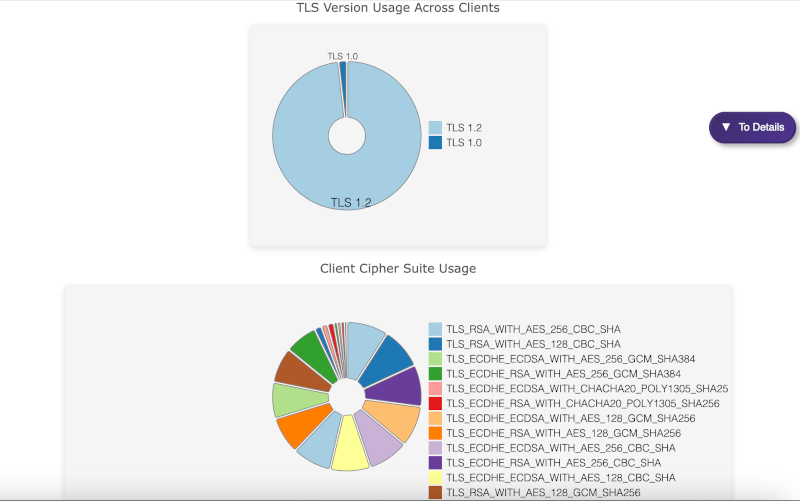
TLS Version Usage Across Clients
The TLS Version Usage Across Clients and Client Cipher Suite Usage screens offer insight into cipher suites and TLS versions, revealing potential weak points in SSL/TLS traffic. PCAP analysis allows for tracking certificate validity, identifying weak encryption, and ensuring secure communication channels. Security teams can act by enforcing stronger encryption standards and renewing expired certificates.
Credential Theft and Password Discovery
Cybercriminals target insecure communication channels to steal sensitive credentials such as usernames and passwords. Protocols like HTTP, FTP, and Telnet transmit data in plaintext, making them vulnerable to eavesdropping attacks.
The HTTP Method Usage and Client Hello / Server Hello screens reveal how PCAP tools like A-Packets visualize HTTP traffic and cipher suite usage. These insights allow network administrators to examine data being exchanged in HTTP GET and POST requests for potential credential exposure.
Through deeper packet inspection, PCAP analysis can uncover plain-text passwords or detect encrypted credentials in protocols like NTLMv2 from SMB traffic. Network professionals can use these insights to prompt password resets, implement stricter encryption standards, and introduce multifactor authentication to secure sensitive data.
Network Scanning and Reconnaissance Attacks
Before launching an attack, cybercriminals often perform network reconnaissance to map out the network, identify live hosts, and scan for open ports. This information-gathering phase is critical for finding weaknesses to exploit.
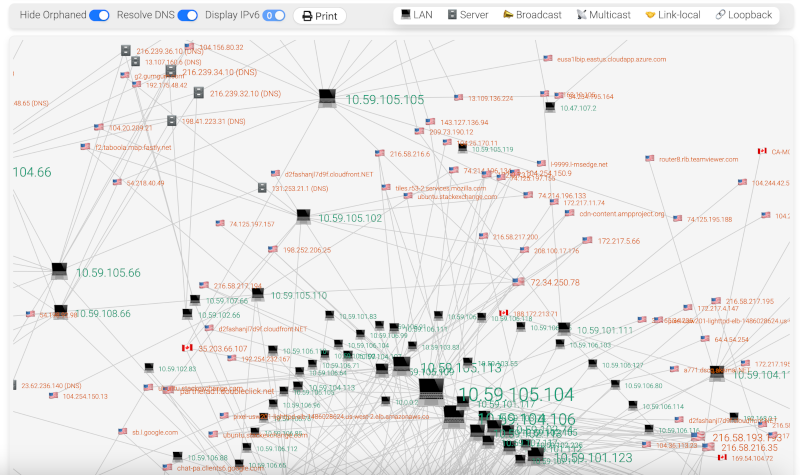
Network Overview
In the Open Ports on Network Nodes and Network Traffic Distribution screens, we see how PCAP analysis can visualize open ports and traffic distribution among endpoints. High volumes of traffic probing open ports or unusual access patterns across multiple devices are tell-tale signs of network scanning.
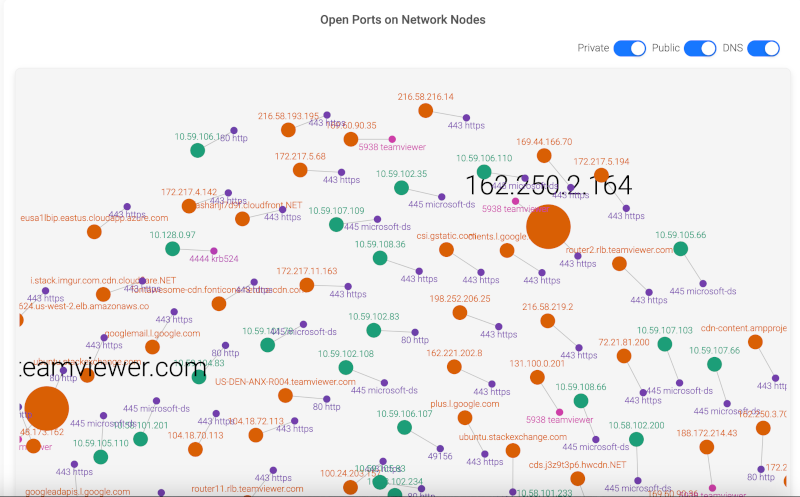
Open Ports
Conclusion: Strengthening Network Defenses with PCAP Analysis
As cyber threats continue to evolve, organizations need robust tools to detect and mitigate security vulnerabilities. PCAP analysis empowers network professionals to identify threats ranging from DNS and ARP spoofing to SSL/TLS attacks, credential theft, and network reconnaissance. By providing real-time insights into network traffic, PCAP tools like A-Packets offer the visibility and control necessary to prevent intrusions and secure communications.
Whether defending against man-in-the-middle attacks or safeguarding sensitive credentials, PCAP analysis is an indispensable part of any network security strategy. Implementing regular packet capture and analysis is essential for staying ahead of emerging threats and maintaining the security of your network infrastructure.