Analyzing SSDP Packets: How to Leverage SSDP Traffic Insights for Network Management and Cybersecurity
In modern networks, the Simple Service Discovery Protocol (SSDP) often operates silently in the background, enabling devices to discover each other and advertise their services seamlessly. Whether it's a smart TV, a network printer, or a router with Universal Plug and Play (UPnP) capabilities, these devices frequently rely on SSDP to communicate device and service information automatically.
For network administrators, security professionals, and IT support teams, understanding and analyzing SSDP traffic can uncover a wealth of information about connected devices, their capabilities, and their vulnerabilities. By reviewing SSDP packets within captured network traffic (PCAP files), you can detect unauthorized devices, discover misconfigurations, or simply map out your ever-growing network.
In this article, we will dive deep into SSDP protocol analysis using our specialized online PCAP parsing tool. We'll explain what SSDP is, why you should analyze it, and how our service can streamline the entire process. Expect to learn:
- The fundamentals of SSDP and its role in network discovery.
- Key details you can extract from SSDP messages.
- Real-world use cases from network troubleshooting to cybersecurity.
- Step-by-step instructions for analyzing SSDP traffic with our online platform.
If you're looking to enhance your network visibility, spot anomalies before they become serious threats, or optimize device discovery, keep reading. By the end of this comprehensive guide, you'll have the know-how to use SSDP data for robust network insights and security.
What Is the SSDP Protocol?
The Simple Service Discovery Protocol (SSDP) is part of the UPnP (Universal Plug and Play) suite of protocols. Its primary purpose is to allow devices on a network to discover each other and offer their services without manual configuration. This makes it straightforward, for instance, for a streaming application to detect a smart TV on the same network.
Key attributes of SSDP include:
- UDP-based: SSDP uses UDP (User Datagram Protocol) for its messages, specifically on port 1900 by default.
- Multicast and Unicast: SSDP employs a multicast address (239.255.255.250) for service discovery, allowing multiple devices to listen for these announcements.
- HTTP-like messaging: Despite using UDP, SSDP messages are structured similarly to HTTP requests and responses, making them human-readable and relatively easy to parse.
Typical SSDP Workflow
- Search: A device sends out an SSDP M-SEARCH request to the multicast address, indicating it's looking for specific device types or services.
- Notify: Devices on the network periodically send NOTIFY messages, announcing their presence or a change in their status.
- Response: When a device receives a search request that matches its capabilities, it sends a HTTP/1.1 200 OK response unicast to the requester.
These three message types - M-SEARCH, NOTIFY, and 200 OK responses - form the core of SSDP communication. By capturing these messages in a PCAP file and analyzing them, we can glean essential information about the devices on a network.
Why Analyze SSDP Packets?
In a world of ever-increasing interconnectivity, analyzing SSDP packets is more than just a curiosity—it's a proactive approach to maintaining a healthy and secure network. Here's why:
Network Visibility
SSDP reveals a host of details about each device, including vendor, product type, software version, and more. This visibility is vital for accurate network inventory and management.
Security Monitoring
Attackers can potentially exploit SSDP or UPnP vulnerabilities to compromise devices or gain unauthorized network access. By monitoring SSDP traffic, security teams can detect abnormal announcements, suspicious device types, or unusual connection behaviors.
Troubleshooting
Missing or misconfigured SSDP packets can break essential discovery and streaming services. Network administrators can quickly home in on where the discovery protocol might be failing, saving hours of guesswork.
Compliance and Audit
For organizations bound by compliance regulations, maintaining logs and analyses of network communications (including SSDP) can be crucial. Inspecting the details of these broadcasts can ensure compliance with data protection and security standards.
Key Information Extracted from SSDP Traffic
When you capture and parse SSDP packets, you can expose a variety of device, service, and configuration details. These details might include:
- Device Descriptions: Such as manufacturer (e.g., “Samsung,” “Cisco,” “HP”), model name, and device type (router, TV, IoT camera, printer, etc.).
- Service Types: Information about which UPnP services the device supports (e.g., media server, WAN IP connection, device management).
- Firmware or Software Versions: Identifying specific firmware versions can be crucial for vulnerability assessments.
- Location of Device Description: SSDP messages often reference a URL hosting the device's XML description, revealing additional configuration or service endpoints.
- Unique Identifiers: These unique identifiers (for instance, uuid:...) can help track devices across reboots or IP address changes.
These details allow system administrators and security experts to pinpoint the device type, understand potential vulnerabilities, and map out network topology with a high degree of detail.
SSDP protocol overview
SSDP Analysis Use Cases
1. Network Administration and Troubleshooting
For a network admin, SSDP traffic offers a bird's-eye view of how devices are spontaneously finding and registering each other. If a critical media streaming service isn't working, analyzing M-SEARCH messages and verifying 200 OK responses can reveal whether the problem lies in the device not announcing its presence, or in the client failing to receive the service advertisement.
In large office networks, where printers and scanners are frequently discovered by employees' computers, a sudden change in SSDP traffic can be the first sign of a misconfiguration. Perhaps a new router is not forwarding multicast traffic as intended, or an old printer's firmware is malfunctioning. Either way, by isolating the SSDP packets, you can quickly zero in on the underlying issue.
2. Cybersecurity and Threat Detection
Attackers often scan for devices running UPnP services because they can provide a bridge into the internal network or an avenue for data exfiltration. Misconfigured routers with open UPnP ports have historically been exploited for DDoS amplification attacks (SSDP amplification).
By analyzing SSDP traffic:
- Security engineers can detect unusual device types sending frequent NOTIFY messages.
- They can identify out-of-place or rogue devices claiming to be a router or a printer.
- They can spot attempts to exploit known SSDP vulnerabilities.
Moreover, certain IoT devices broadcast very specific SSDP messages that might contain default or known-vulnerable firmware versions. By capturing and analyzing these, you can hone in on vulnerable endpoints before attackers do.
3. Device Discovery and Inventory
With the rapid expansion of IoT, it's more challenging than ever to maintain an up-to-date network inventory. Many devices may only partially comply with traditional network discovery methods like SNMP or ICMP. SSDP, however, is widely adopted in consumer and small-office IoT gear.
If you're building a device inventory, analyzing SSDP packets can highlight:
- All the smart TVs on your network (useful in a corporate environment for video conferencing or in hospitality settings).
- Routers and access points broadcasting UPnP capabilities.
- Switches with management or discovery features enabled.
- Any hidden devices inadvertently placed on the network by employees (e.g., personal IoT gadgets).
How A-Packets Simplifies SSDP Packet Analysis
Our online SSDP packet analysis tool is designed to simplify the process of parsing and interpreting SSDP traffic. Below are the key features that make our tool indispensable for network administrators, cybersecurity professionals, and engineers:
Comprehensive Visualization
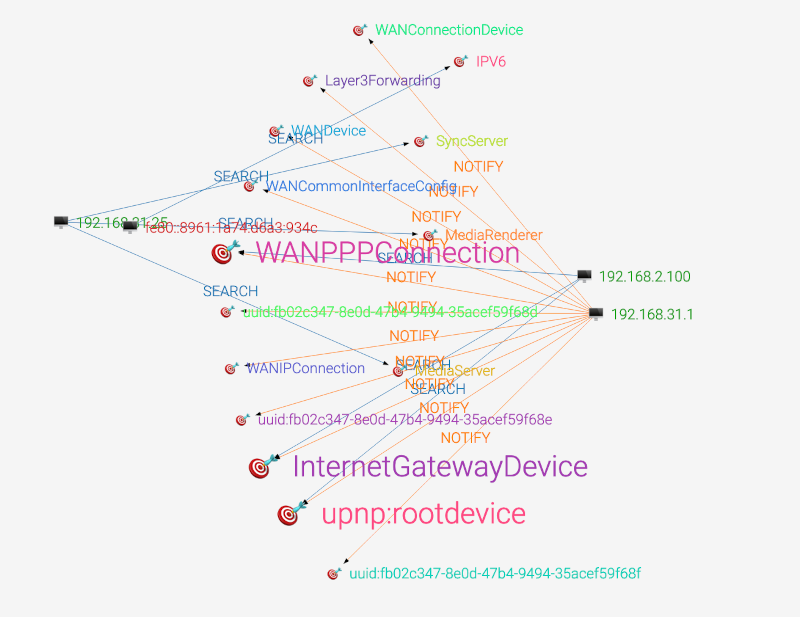
A-Packets dissects SSDP packets into their individual components, providing detailed insights into the critical information contained within each packet. This granular breakdown allows you to examine several aspects of the communication, starting with device and service types. Each SSDP packet includes details about the broadcasting device, such as whether it's a router, media server, printer, or IoT appliance, along with the services it offers. This is crucial for understanding the role each device plays in the network and how they interact with others.:
- Device Profiles: Identify different types of devices, such as routers, smart TVs, printers, or switches.
- Request and Response Flows: Monitor both SSDP requests and the responses they generate, helping you better understand the interaction between devices.
- Node Information: Each node in the network is represented with details such as IP address, device name, manufacturer, and software version.
Detailed Packet Breakdown
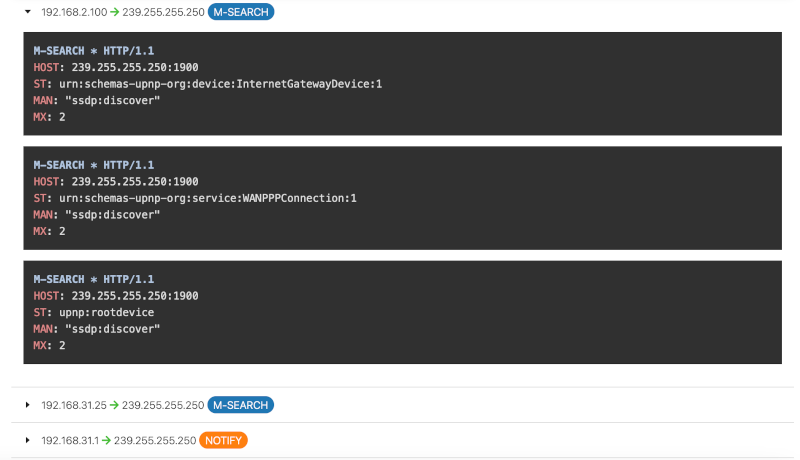
Our tool breaks down SSDP packets into their individual components, giving you insights into:
- Device and Service Types: Each SSDP packet reveals the type of device broadcasting and the services it offers. For example, an SSDP response might indicate the presence of a media server or printer.
- Software Versioning: SSDP broadcasts often include version information for installed software and firmware, allowing you to track outdated systems that may need updating.
- HTTP Headers: SSDP packets contain HTTP-like headers, and our tool provides detailed visibility into these headers for further inspection and debugging.
SSDP protocol details
Detecting Anomalies and Unauthorized Devices
Security is a significant concern when dealing with SSDP traffic due to its broadcast nature, which can be exploited by attackers. Our tool helps detect rogue devices that may have been introduced into the network without authorization, allowing for swift action. It also highlights misconfigured UPnP devices, which can expose vulnerabilities, and flags abnormal traffic patterns that could indicate potential DDoS amplification attacks, enabling security teams to respond to threats before they escalate.:
- Rogue Devices: Devices that shouldn't be on the network will stand out during SSDP packet analysis. By cross-referencing known and unknown devices, you can quickly detect any unauthorized presence.
- Misconfigured UPnP Devices: Misconfigured devices can expose your network to vulnerabilities, but our tool highlights unusual behavior that may indicate an improperly configured device.
- DDoS Amplification Attempts: SSDP can be used in reflection-based DDoS attacks. Our tool monitors traffic patterns and flags suspiciously large amounts of SSDP responses or requests, enabling cybersecurity teams to take swift action.
Customized Reporting and Alerts
Once you've analyzed the SSDP packets, our tool allows you to generate customized reports that summarize:
- Device Lists: A full list of all devices broadcasting on SSDP, including their IPs, software, and hardware information.
- Alerts: Set custom alerts for specific types of anomalies or device behavior. For example, you could configure the tool to alert you if a new device joins the network or if a known vulnerability is detected in a device's software.
- Traffic Trends: Monitor SSDP traffic over time to detect any unusual spikes or drops, which might indicate network issues or security threats.
How to Get Started with SSDP Packet Analysis on Our Tool
To analyze SSDP traffic with our tool, follow these steps:
- Upload Your PCAP File: Start by uploading a packet capture (PCAP) file containing the SSDP traffic you wish to analyze.
- Select SSDP Protocol: Once uploaded, filter the packet capture by selecting the SSDP protocol for targeted analysis.
- Visualize the Data: Our tool will automatically map out the devices, nodes, and interactions captured in the SSDP traffic, making it easy to identify network devices and their communications.
- Generate Reports: After visualizing the data, you can generate detailed reports to summarize device presence, identify vulnerabilities, and track anomalies.
Best Practices for SSDP Monitoring and Management
Regularly Capture and Analyze
Don't wait for a problem to arise before capturing SSDP traffic. Regular analysis can help you spot trends and anomalies early.
Restrict External Access
SSDP was primarily designed for local networks, not for the open internet. Ensure your edge devices (firewalls, routers) aren't exposing SSDP to untrusted external sources.
Use Multicast Properly
Multicast must be correctly configured on switches and routers. If devices cannot receive SSDP announcements or if the network floods with them, it usually indicates a multicast misconfiguration.
Keep Firmware Updated
IoT devices often rely on SSDP for initial setup. Outdated firmware can leave these devices vulnerable. By scanning for old firmware versions in SSDP messages, you can flag devices that need immediate patching.
Implement Segmentation
Consider segmenting IoT devices onto a separate VLAN. This way, you can monitor SSDP traffic within that VLAN more effectively and reduce the blast radius if something goes wrong.
Monitor for DDoS Indicators
SSDP is known to be exploited for amplification attacks. If you see a surge in outbound SSDP traffic to unexpected IPs, investigate immediately.
Conclusion
The Simple Service Discovery Protocol (SSDP) may operate quietly behind the scenes, but the data it carries is invaluable for anyone tasked with managing, securing, or troubleshooting a network. From discovering the latest smart devices to pinpointing vulnerabilities in outdated firmware, SSDP analysis provides deep visibility into network endpoints.
Our online PCAP parsing service takes the complexity out of SSDP analysis. By automatically detecting SSDP messages, visualizing device relationships, and flagging anomalies, our platform empowers you to make rapid and informed decisions about your network. Whether you're responsible for a small business network or a sprawling enterprise environment, integrating SSDP analysis into your regular monitoring routine can yield substantial benefits—from strengthened cybersecurity to optimized device deployment.
Ready to get started? Head over to our platform, upload a PCAP file, and begin uncovering the hidden gems in your SSDP traffic. With the right insights at your fingertips, you'll be well-equipped to maintain a secure, efficient, and future-proof network.