Using PCAP Analysis for Network Forensics
In the digital age, network security and incident response have become critical priorities for organizations of all sizes. When a security breach occurs, the first step is to understand how it happened, identify the affected systems, and mitigate any ongoing risks. One of the most effective tools for this process is PCAP (Packet Capture) analysis. PCAP files store raw network traffic data, allowing forensic investigators to retrace events, examine communications, and uncover potential anomalies or malicious activities.
In this article, we'll explore how PCAP analysis can aid in network forensics, and how tools like A-Packets simplify the process. We'll demonstrate how to use A-Packets as a PCAP file viewer and PCAP analyzer to facilitate forensic investigations.
What is PCAP Analysis and Why is it Important for Network Forensics?
PCAP (Packet Capture) analysis involves examining captured network traffic data to gain insights into network behavior, detect anomalies, and investigate incidents. A PCAP file contains detailed records of every data packet that passed through a monitored network interface, preserving metadata about the packet source, destination, protocol, and timestamp. This data is invaluable for forensic investigators because it allows them to reconstruct events and understand the specifics of network interactions.
Key Uses of PCAP Analysis in Network Forensics:
- Incident Response and Breach Investigation: PCAP analysis allows forensic investigators to trace how attackers entered the network, which systems they accessed, and what data may have been exfiltrated.
- Threat Hunting: By analyzing network traffic patterns, investigators can identify suspicious activity that may indicate a compromised system or an ongoing attack.
- Network Anomaly Detection: PCAP data can reveal unusual traffic patterns, such as unexpected data transfers or unauthorized communications, which are often indicators of malware or insider threats.
- Legal and Compliance Evidence: PCAP files provide a reliable and timestamped record of network activity, which can be used as evidence in legal or compliance audits.
Introduction to A-Packets: A Powerful PCAP File Viewer and Analyzer
A-Packets is a versatile and user-friendly PCAP file viewer and PCAP analyzer designed to assist network administrators, cybersecurity professionals, and forensic investigators. Unlike many traditional tools that require complex configurations, A-Packets provides a web-based interface, allowing users to upload PCAP files and analyze them directly in the browser.
Key features of A-Packets include:
- Protocol Analysis: A-Packets supports protocols like HTTP, DNS, SSL/TLS, ARP, and many others, providing deep insights into the details of each packet.
- Network Mapping: Visualize the structure of your network, identifying connections between nodes, devices, and the direction of traffic flow.
- Detailed Traffic Analysis: Break down traffic by IP addresses, protocols, and session details to understand network interactions at a granular level.
- Security Alerts and Anomaly Detection: A-Packets flags potential security issues like expired certificates, weak encryption algorithms, and unusual traffic patterns, assisting in threat detection.
Let's explore how A-Packets can be used in real-world network forensics scenarios.
Step-by-Step Guide to Using A-Packets for Network Forensics
Step 1: Upload and View Your PCAP File
The first step in analyzing network traffic with A-Packets is to upload your PCAP file. The process is straightforward:
- Visit the A-Packets website.
- Click on the "Upload PCAP" button and select your file.
- Once the file is uploaded, A-Packets automatically begins parsing the data, displaying an overview of the network traffic.
With A-Packets' intuitive interface, you can start investigating your network data immediately. The platform categorizes information based on protocols, making it easy to locate specific types of traffic, such as DNS queries or HTTP requests.
Step 2: Use Protocol Filters to Narrow Down Analysis
In forensic investigations, it's essential to focus on relevant traffic, as PCAP files can contain vast amounts of data. A-Packets provides powerful filtering options, allowing you to zero in on specific protocols or activities.
For instance, if you're investigating a DNS-based attack, you can filter for DNS traffic and ignore unrelated data. Similarly, if you suspect an SSL/TLS vulnerability, you can focus on SSL/TLS traffic and inspect encryption details and certificate validity.
Example Use Case: Analyzing DNS Traffic for Signs of DNS Spoofing
DNS spoofing attacks are common in network breaches. By filtering for DNS traffic, A-Packets allows you to examine each query and response. You can look for inconsistencies, such as DNS responses that don't match the requested IP or abnormal spikes in DNS requests, which might indicate DNS tunneling or spoofing.
Step 3: Visualize Network Structure and Communication Flow
A-Packets offers a unique feature: Interactive Network Mapping. This visualization displays the communication flow between devices on the network, identifying each node and showing which devices communicated with each other.
This is particularly useful for identifying compromised devices or unusual communication patterns. For example, if you notice that an internal device is communicating with an unknown external IP, this could be an indication of command-and-control (C&C) activity.
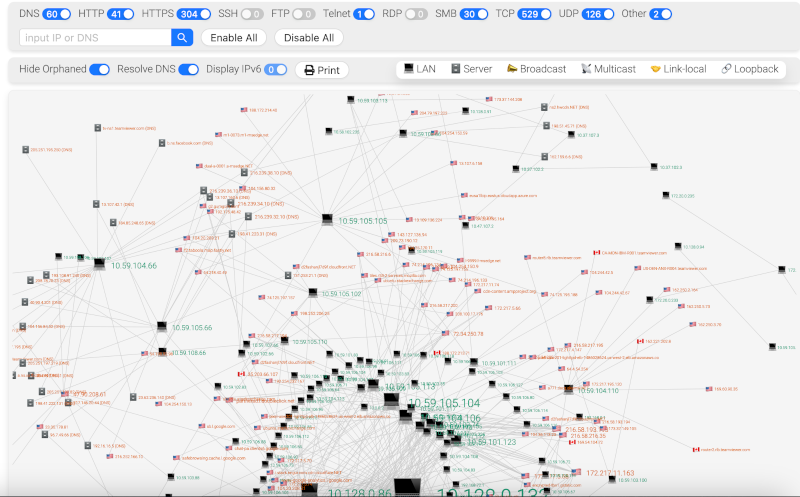
Network Mapping Visualization
Description: In the Network Mapping view, A-Packets shows connections between internal and external IPs, highlighting unusual communication patterns. This can help forensic investigators pinpoint suspicious devices or identify which machines were compromised in a breach.
Step 4: Analyze SSL/TLS Sessions for Certificate and Encryption Issues
SSL/TLS traffic is commonly used to secure data, but misconfigurations can expose a network to vulnerabilities like expired certificates or weak ciphers. A-Packets inspects SSL/TLS sessions and flags any issues with encryption or certificate validity.
For instance, if a certificate is expired or self-signed, A-Packets will display an alert. Additionally, the platform provides information about the cipher suite used in each session, enabling you to identify sessions with outdated or insecure algorithms.
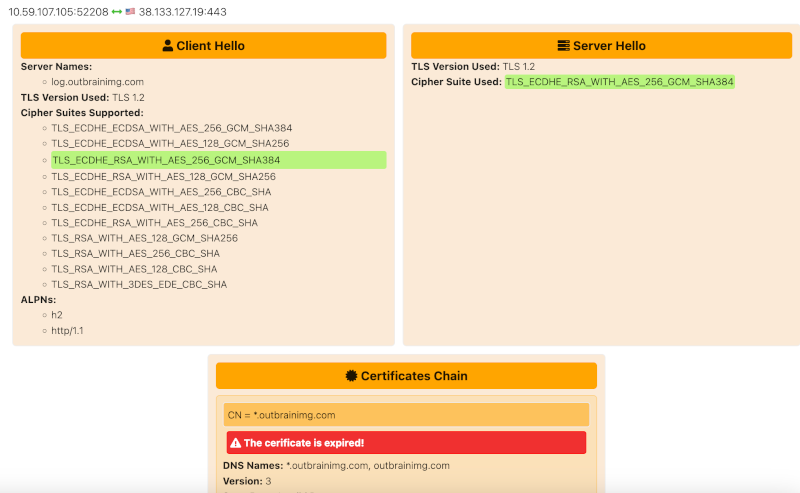
SSL/TLS Session Analysis
Description: A-Packets displays SSL/TLS session details, including protocol versions, cipher suites, and certificate information. This helps forensic investigators detect expired certificates or weak encryption that could expose the network to attacks.
Step 5: Reconstruct Events with HTTP and SMB Traffic Analysis
HTTP and SMB protocols are commonly used in network communications, but they can also be exploited by attackers. A-Packets allows forensic investigators to examine HTTP requests, responses, and headers in detail, as well as SMB traffic for file shares and NTLM authentication.
For example, by analyzing HTTP traffic, you might detect unauthorized data exfiltration, where sensitive information is sent out to an external server. SMB traffic, on the other hand, can reveal brute-force login attempts or file access patterns, which may indicate compromised credentials.
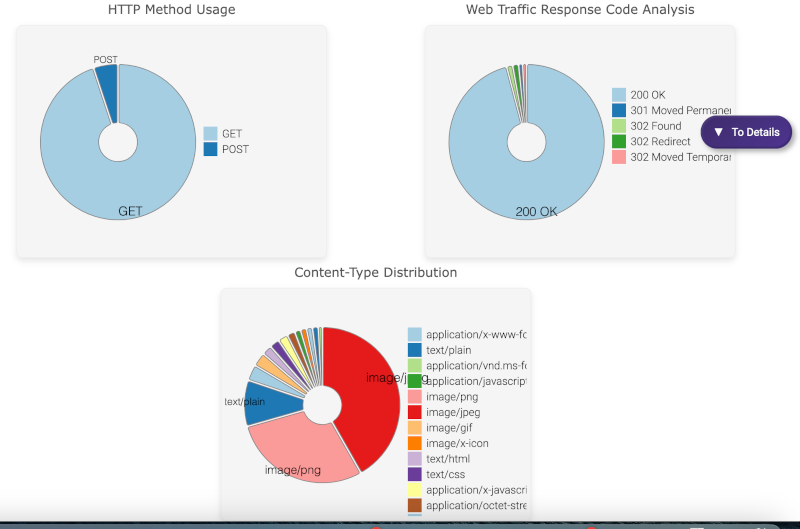
HTTP Traffic
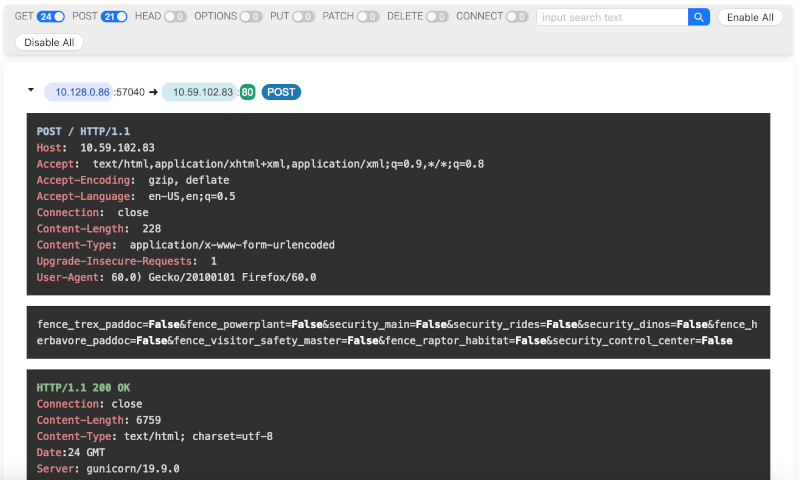
HTTP Traffic Breakdown
Description: This view in A-Packets displays HTTP requests and responses, including detailed headers and payload data. Forensic investigators can use this information to identify data exfiltration attempts or unauthorized access.
Leveraging A-Packets for Incident Response and Threat Hunting
A-Packets is more than just a PCAP file viewer; it's a robust tool for proactive network security. By incorporating it into your incident response workflow, you can enhance your organization's ability to detect, investigate, and mitigate network threats.
Automated Alerts for Security Anomalies
A-Packets offers automated alerts for specific security anomalies, such as expired SSL certificates or unusual traffic patterns. These alerts allow security teams to respond quickly to potential threats, minimizing the impact of a breach.
Historical Data Analysis for Threat Hunting
PCAP files can serve as a record of network activity over time. A-Packets enables you to archive and review old PCAP files, allowing you to identify trends or recurring suspicious behavior. This is invaluable for threat hunting, where investigators proactively search for signs of malicious activity before it becomes a major issue.
Why Choose A-Packets as Your PCAP Analyzer?
A-Packets stands out as a powerful PCAP file viewer and PCAP analyzer for several reasons:
- User-Friendly Interface: Unlike traditional PCAP analysis tools, A-Packets is easy to use, even for users with limited technical expertise.
- Comprehensive Protocol Support: A-Packets supports a wide range of protocols, including DNS, HTTP, SSL/TLS, ARP, and SMB, enabling thorough forensic investigations.
- Real-Time Alerts: Automated alerts for expired certificates, weak encryption, and unusual traffic patterns help you respond quickly to potential threats.
- Interactive Visualizations: The network mapping and SSL/TLS session views provide visual insights that simplify complex data, making it easier to understand and act on findings.
Conclusion: Enhancing Network Forensics with A-Packets
PCAP analysis is a vital part of network forensics, helping investigators understand the details of network incidents, identify compromised devices, and detect potential vulnerabilities. With A-Packets, organizations can efficiently analyze PCAP files, monitor network traffic, and proactively respond to security incidents.
Whether you're an IT professional, network administrator, or cybersecurity expert, A-Packets provides the tools you need to investigate incidents, detect threats, and secure your network. If you're looking for a reliable and user-friendly PCAP file viewer and PCAP analyzer, try A-Packets to enhance your network forensics capabilities.