How to Analyze Encrypted Traffic in PCAP Files: A Guide with A-Packets
Encrypted traffic is a cornerstone of secure communications, protecting data as it moves through the network. Monitoring this traffic is crucial for identifying anomalies that could indicate potential security breaches, misconfigurations, or outdated encryption methods. While encrypted data itself cannot be decrypted without the appropriate keys, PCAP analysis tools like A-Packets offers valuable insights into the metadata and patterns of encrypted sessions, helping network administrators spot vulnerabilities before they are exploited.
This article explores how A-Packets analyzes encrypted traffic in PCAP files, focusing on what information can be gathered without decrypting the traffic itself. We'll delve into monitoring SSL/TLS sessions, identifying expired certificates, evaluating cipher suites, and detecting vulnerabilities such as the Heartbleed attack. By the end of this article, you will understand the key aspects of encrypted traffic monitoring and how to leverage A-Packets to protect your network.
Understanding SSL/TLS Metadata in PCAP Files
SSL/TLS is the most widely used protocol for securing data transmitted over the internet. When inspecting encrypted traffic through PCAP files, the focus is not on decrypting the data but on analyzing the metadata available within the session, such as:
- Client and Server Hello Messages: These messages initiate the SSL/TLS handshake and reveal important details about the encryption algorithms and protocol versions supported by both client and server.
- Certificate Information: The server sends its digital certificate to the client during the handshake process, which includes details like the certificate's validity period, issuer, and public key.
- Cipher Suite Negotiation: The client and server agree on a cipher suite, which defines the algorithms used for encryption, hashing, and key exchange.
A-Packets captures this metadata and presents it visually, allowing network administrators to observe and evaluate the security of encrypted sessions without needing to decrypt the traffic itself.
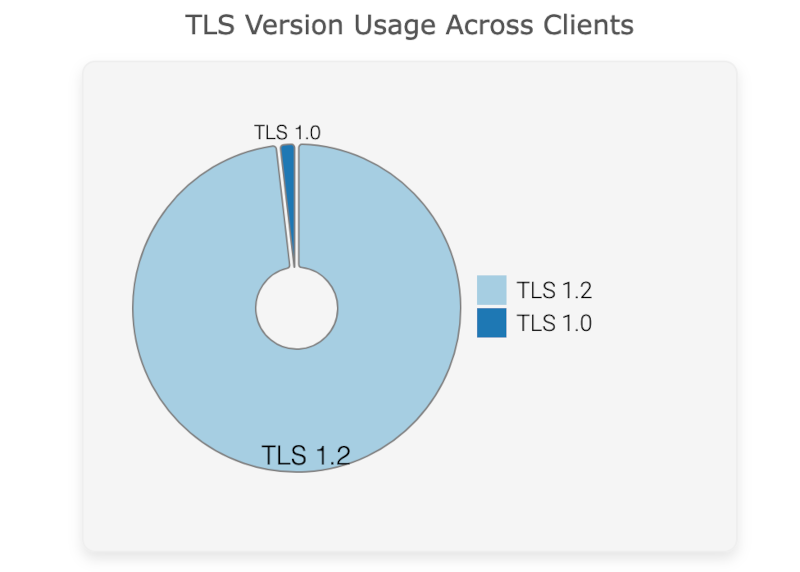
TLS Version Usage Across Clients
In this visualization, A-Packets provides a detailed breakdown of the TLS versions used across different sessions in the network. By inspecting these details, administrators can identify outdated protocols (e.g., TLS 1.0) that may expose the network to vulnerabilities and weak encryption methods.
Monitoring Expired or Self-Signed Certificates
Certificates play a critical role in SSL/TLS, ensuring that the communicating parties are who they claim to be. However, expired or self-signed certificates can undermine the trustworthiness of the encryption.
A-Packets scans PCAP files for SSL/TLS sessions and flags any instances where certificates have expired or are self-signed. This alert feature is vital, as expired certificates can leave encrypted sessions vulnerable to man-in-the-middle (MitM) attacks.
Example Use Case:
Imagine a scenario where a critical business application continues to operate with an expired SSL certificate. Attackers can exploit this situation by intercepting the connection and impersonating the server. With A-Packets, you can detect and respond to these issues swiftly, ensuring that certificates are updated or replaced, maintaining the integrity of your encrypted traffic.
Evaluating Cipher Suite Security
The choice of cipher suite determines the strength of encryption and the overall security of an SSL/TLS session. Some cipher suites are considered weak and outdated, leaving networks vulnerable to attacks. For instance, cipher suites using RC4 or DES algorithms are now deemed insecure and should be replaced with more robust options like AES-GCM.
A-Packets provides an overview of the cipher suites negotiated during SSL/TLS handshakes. Network administrators can see which encryption algorithms are being used and whether they meet modern security standards. A visual representation of the cipher suite distribution helps administrators quickly identify if insecure algorithms are still in use.
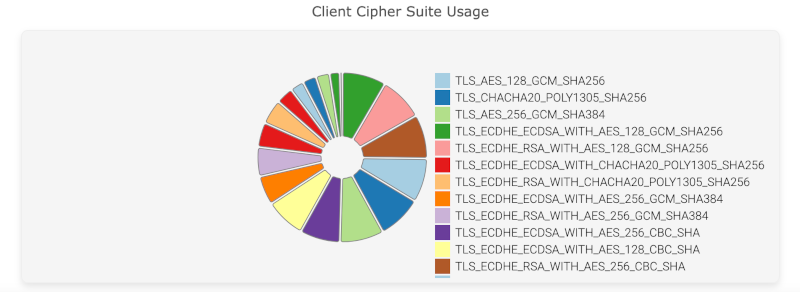
Client Cipher Suite Usage
A-Packets displays the various cipher suites used by clients in the network. By monitoring these details, administrators can pinpoint sessions where weak or deprecated cipher suites are being used and take corrective action, such as enforcing stronger encryption policies or upgrading outdated software.
Detecting Heartbleed and Other Vulnerabilities
One of the most infamous vulnerabilities in SSL/TLS history is the Heartbleed bug, which affected versions of OpenSSL and allowed attackers to read sensitive data from a server's memory. While PCAP analysis cannot directly decrypt encrypted traffic, it can detect patterns or anomalies that indicate an exploit attempt.
A-Packets scans for known vulnerabilities in the SSL/TLS handshake process, such as Heartbleed. If the tool detects unusual behavior - like repeated and suspicious heartbeat requests - it will alert the administrator. Such behavior is often associated with attacks that try to exploit vulnerabilities in the SSL/TLS implementation. You can find more information about alerts here
Real-World Application: An administrator using A-Packets can set up monitoring rules to detect handshake anomalies that align with known attack patterns. For example, if an unusually high number of heartbeat requests is detected from a specific client, the tool can trigger an alert, prompting further investigation into the source of the traffic.
Visualizing Encryption Traffic Patterns
A-Packets offers more than just text-based analysis; it provides visual insights into SSL/TLS traffic patterns that allow network professionals to understand how encrypted traffic flows through their network. By plotting encryption sessions and showing the details of each connection, including client and server information, encryption protocols, and certificate details, administrators can get a bird's-eye view of their network's encryption landscape.
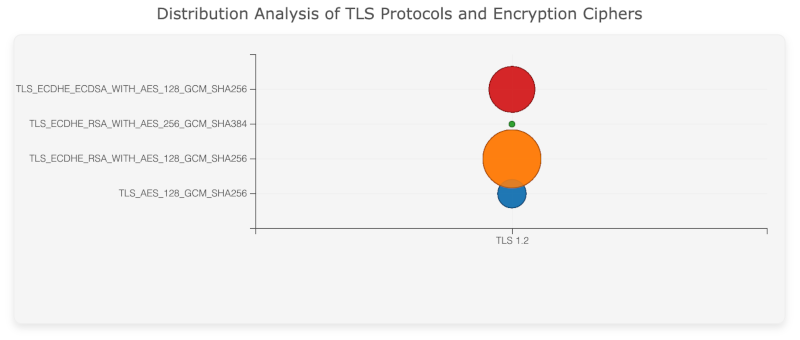
Distribution Analysis of TLS Protocols and Encryption Ciphers
In this screenshot, A-Packets presents a bubble chart that shows the usage distribution of different TLS versions and ciphers across the network. Visualizing this information allows administrators to quickly identify whether the majority of their network traffic uses strong and up-to-date encryption protocols or if there are legacy protocols that need to be phased out.
Proactive Monitoring and Automated Alerts
Proactive monitoring is essential in today's cybersecurity landscape. A-Packets enables administrators to set up alerts for specific SSL/TLS anomalies, such as the use of weak cipher suites, expired certificates, or known vulnerabilities like Heartbleed. These alerts empower network professionals to act quickly and address potential threats before they escalate.
Automated alerts can be customized based on the organization's security policies. For example, an alert can be configured to trigger if any client attempts to negotiate a connection using an obsolete version of SSL/TLS. This allows the IT team to investigate and remediate the issue before attackers exploit it.
Compliance and Security Audits
Organizations often need to demonstrate compliance with security standards, such as PCI-DSS, HIPAA, or GDPR, which require the use of strong encryption to protect sensitive data. A-Packets can be an invaluable tool for compliance teams, as it allows them to verify the security of encrypted sessions, ensuring that only approved protocols and cipher suites are used.
By providing detailed logs and visualizations of encryption usage, A-Packets helps organizations pass security audits and maintain compliance with regulatory requirements. Administrators can generate reports that highlight areas of improvement or confirm that the network meets security benchmarks.
Conclusion: The Value of Analyzing Encrypted Traffic with A-Packets
While encrypted traffic cannot be decrypted without the proper keys, analyzing its metadata and behavior provides valuable insights into network security. Tools like A-Packets make it possible to detect vulnerabilities, monitor encryption standards, and ensure compliance - all without compromising the confidentiality of the encrypted data itself.
Through A-Packets' features - such as monitoring SSL/TLS sessions, flagging expired certificates, visualizing encryption protocols, and alerting for vulnerabilities like Heartbleed - network administrators can stay ahead of threats and maintain a secure network environment. By leveraging PCAP analysis for encrypted traffic, organizations can proactively safeguard their communications and protect sensitive data.
If you're looking to strengthen your network's defenses and ensure that your encryption methods meet the highest security standards, start using A-Packets today for comprehensive PCAP analysis.